What is .xtbl ransomware?
Ransomware is a type of malware that most definitely plays on our weaknesses. It works by kidnapping your files and holding them hostage � or freezing them, rendering them inaccessible. Subsequently it will demand that you pay a ransom in order to be given access to a code that will enable you to unlock, or decrypt, them. The ransom note will either be sent to you by email or displayed on your computer screen. It's a tried and tested method of extortion that dates back to time immemorial � albeit in a repackaged format for the twenty first century. What makes this ransom virus deffirent from others is the .xtbl file extension which indicates with exactly which ransomware you are dealing with. There are obviously more than one: CryptoWall 3.0, CryptoLocker, CTB-Locker and others. Once your files are encrypted you will see a red text in black background saying that you must read README.txt for more information. There can be up to 10 README.txt files on your desktop.
Attention!
All the important files on your disks were encrypted.
The details can be found in README.txt files which you can find on any of your disks.
The README.txt reads:
???? ????? ???? ???????????.
????? ???????????? ??, ??? ?????????? ????????? ???:
[edited]
?? ??????????? ????? decode010@gmail.com ??? decode1110@gmail.com.
????? ?? ???????? ??? ??????????? ??????????.
??????? ???????????? ?????????????? ?? ???????? ?? ? ????, ????? ????????????? ?????? ??????????.
All the important files on your computer were encrypted.
To decrypt the files you should send the following code:
[edited]
to e-mail address decode010@gmail.com or decode1110@gmail.com.
Then you will receive all necessary instructions.
All the attempts of decryption by yourself will result only in irrevocable loss of your data.
Basically, you have to email your code to ecode010@gmail.com or decode1110@gmail.com in order to get further instructions. Cyber criminals change email addresses quite often, so yours might be different. They were previously using deshifrovka@india.com and deshifrator01@gmail.com.
Here's how the encrypted files look like:
The virus appends .xtbl file extension to ALL files and in some cases even renames all the files. At the moment, there's no way to actually decrypt files unless you have a super computer and can brute force every possible decryption key to decrypt your files. I bet you don't have it, so you can either restore your files from backups or pay the ransom. If you don't have backups then you can use a few tools listed below to recover at least some of your files.
How does .xtbl encryption virus infect your PC?
It sticks to its traditional roots by normally spreading itself either via an email attachment. However it may also attack you through a website that has been infected with it or, as is often the case with malware, by being packaged with another program.
The best form of protection against .xtbl virus is to be cautious
The rich and the famous might have to take the risk of being kidnapped seriously, but for you and I, it is probably not something that figures much in our day to day lives. I don't know about you but I know I'm probably not a high risk target (I hope I don't live to regret saying that!) �besides, I am not sure who a kidnapper would contact to get any kind of decent ransom for me! However, being careful when you're online is something that all of us should do � regardless of our status, power, fame or riches. And that means not opening email attachments from unknown senders. Being careful when opening email attachments EVEN if you know the sender (they could have been hacked), and not downloading programs or files from third party or dubious looking websites.
XTBL virus can be extremely convincing and has been designed to play on our fears. The fear that we will lose valuable data or the fear that we are being monitored or about to get in serious trouble.
What should I do if I've been infected?
It's easy to say, but try not to panic. And whatever you do, don't pay the ransom unless the encrypted files are very important and you can't afford to lose them. If the encrypted files are not very important or you don't have money to pay the ransom, you can remove try to restore your files (at least some of them) using Shadow Explorer, Recuva and some other specialized tools listed below. Please note that even of you decide to pay the ransom there's really no guarantee that cyber crooks will recover your files. If you have any questions, please leave a comment below. Last, but not least, if there's anything you think I should add or correct, please let me know. It might be a pain but the issue needs to be dealt with � and the way to do it is by not giving in, not paying up and not letting the attackers win.
Written by Michael Kaur, http://deletemalware.blogspot.com
Step 1: Removing .xtbl and related malware:
Before restoring your files from shadow copies, make sure XTBL virus is not running. You have to remove this malware permanently. Thankfully, there are a couple of anti-malware programs that will effectively detect and remove this malware from your computer.
1. First of all, download and install recommended anti-malware scanner. Run a full system scan and remove detected malware.
2. Then, download ESET Online Scanner and run a second scan to make sure there are no other malware running on your computer.
That's it! Your computer should be clean now and you can safely restore your files. Proceed to Step 2.
Step 2: Restoring files encrypted by .xtbl virus:
Method 1: The first and best method is to restore your files from a recent backup. If you have been regularly performing backups, then you should use your backups to restore your files.
Method 2: Try to restore previous versions of files using Windows folder tools. To learn more, please read Previous versions of files.
Method 3: Using the Shadow Volume Copies:
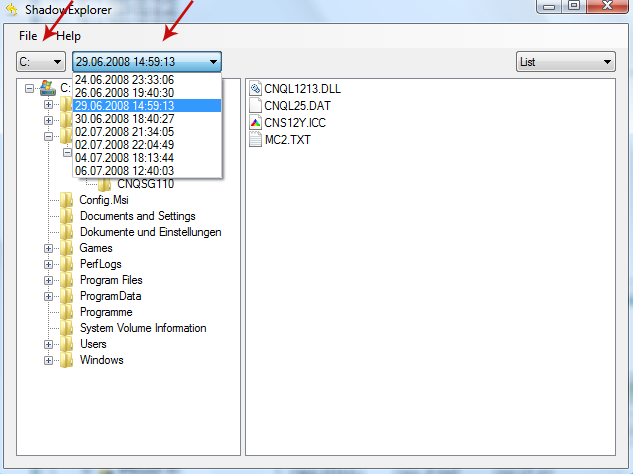
1. Download and install Shadow Explorer. Note, this tool is available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8.
2. Open Shadow Explorer. From the drop down list you can select from one of the available point-in-time Shadow Copies. Select drive and the latest date that you wish to restore from.
3. Righ-click any encrypted file or entire folder and Export it. You will then be prompted as to where you would like to restore the contents of the folder to.
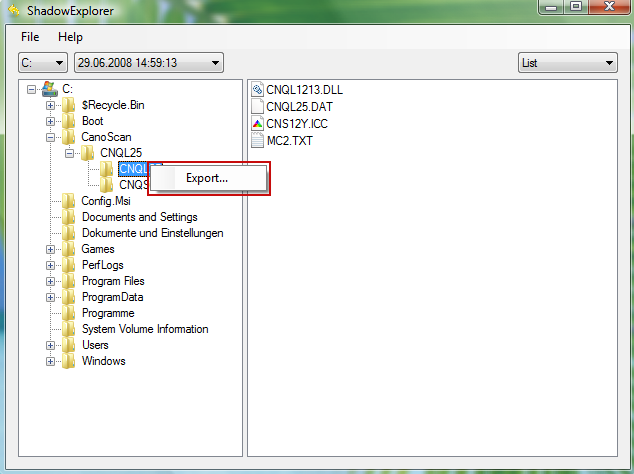
Hopefully, this will help you to restore all encrypted files or at least some of them.




0 Response to "Remove .xtbl Virus and Restore Encrypted Files"
Post a Comment